The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Detection Rule Validation
In recent years, the volume of alerts and logs that security teams have to deal with has increased exponentially. Organizations are collecting more data than ever before, while new and increasingly sophisticated threats are constantly emerging. In this cycle, creating new detection rules becomes increasingly difficult. Detection Rule Validation (DRV) allows security teams to maintain control over detection rules and automate manual detection engineering processes to achieve continuous and proactive rule validation.
PRODUCT DESCRIPTION
Detection Rule Validation (DRV) is a solution that proactively identifies problems related to the performance and hygiene of SIEM rules, providing information that accelerates threat detection and response. DRV enables continuous validation and optimization of detection rules, ensuring that they are effective in detecting real threats while minimizing the number of false positives.
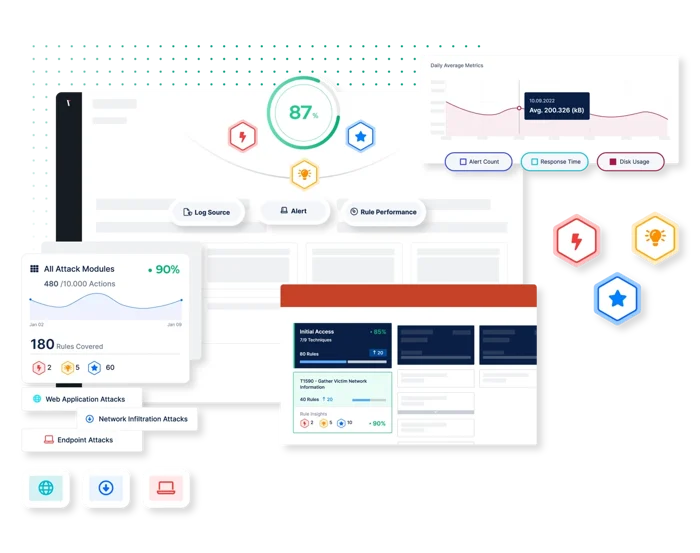
DRV analyzes detection rules for quality, performance, and threat coverage, and then provides detailed reports and analyses that help identify areas for improvement. This allows security teams to focus on what matters most, which is the proactive validation of rules and optimization of threat detection.
FUNCTIONALITIES
- Continuous and proactive rule validation: Continuously detect improvement points in the rule baseline and prioritize rules to ensure that the right rules are in place and that alerts are triggered for critical security events.
- Performance and security insights: Reveal threat gaps by measuring the threat coverage of your rules and analyzing deficiencies.
- Extensive library of real-world threats: Test the performance of your detection rules against thousands of real-world threats, updated daily.
- MITRE ATT&CK mapping: To help visualize threat coverage and visibility, the Picus platform automatically maps simulation results against the MITRE ATT&CK framework.
- Assess the quality of your detection rules: Identify broken, missing, and inconsistent rules and any issues that need immediate attention by assessing the rule baseline quality.
- Flag a missing or broken rule to help drive corrective action and prevent future problems.
- Technology integrations for Detection Rule Validation: Integrations with leading security vendors help improve the detection engineering process for building, testing,
IT solutions

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30












