The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Security Control Validation
Security Control Validation (SCV) from PICUS is a tool that allows for an objective assessment of the effectiveness of existing IT security measures. Through continuous verification and simulation of realistic attacks, SCV enables proactive detection and elimination of vulnerabilities in the system before they are exploited by cybercriminals. Moreover, SCV utilizes the well-known and respected MITRE ATT&CK matrix in the cybersecurity industry, which allows for an even better understanding and assessment of potential threats.
PRODUCT DESCRIPTION
SCV operates by simulating real-world attacks, verifying if existing security mechanisms can effectively block them. This solution consists of a library of predefined attack scenarios that can be customized to the specific needs of the organization, and also maps attack techniques from the MITRE ATT&CK matrix.
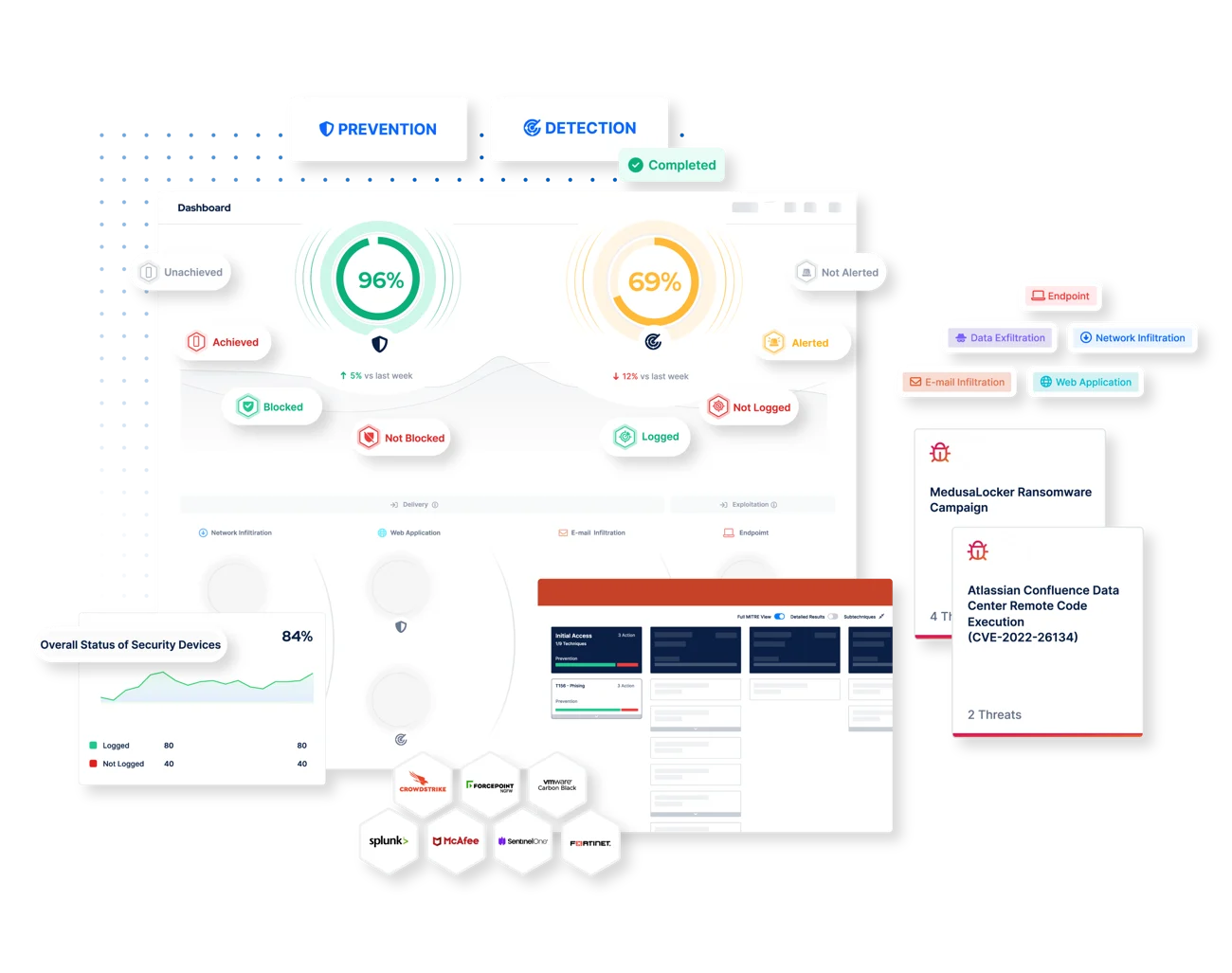
Attack simulations in the Threat Library can be divided into:
- Network Infiltration: Simulation of attempts to break into the internal network, e.g., by exploiting security vulnerabilities.
- EndPoint: Testing the security of endpoint devices (computers, laptops) against various types of malware.
- Web Application Firewall: Simulation of attacks on web servers, such as SQL injection, cross-site scripting, to check the effectiveness of the web application firewall (WAF).
- Data Exfiltration: Simulation of attempts to steal data from the organization, for example, by exploiting security vulnerabilities.
- Email Infiltration: Testing email security against various types of attacks, such as phishing, malicious attachments, or links leading to infected websites.
- URL Filtering: Simulation of attempts to access harmful or unwanted websites to check the effectiveness of URL filtering.
SCV integrates with the existing security infrastructure, providing detailed reports and analyses that help understand where weaknesses exist and how to fix them.
FUNCTIONALITIES
- Continuous security control validation: Regular tests allow for ongoing monitoring of security effectiveness and identification of new vulnerabilities.
- Realistic attack simulation: SCV uses authentic attack techniques to accurately assess how the system will behave in the face of a real threat.
- Scenario customization: The ability to create custom attack scenarios allows for security testing in the context of specific threats the organization may encounter.
- Detailed reports and analyses: SCV provides transparent information about test results, facilitating the identification of areas for improvement and understanding which attack techniques may be effective against the given infrastructure.
- Integration with existing infrastructure: SCV seamlessly cooperates with various security tools, minimizing disruptions to system operation.
- Utilization of MITRE ATT&CK: SCV allows for the assessment of security effectiveness in the context of the latest attack techniques described in the MITRE ATT&CK matrix, enabling a better understanding of risk and prioritization of remediation actions.
IT solutions

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30












