The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Skyhigh Security Secure Web Gateway (SWG)
Skyhigh Secure Web Gateway (SWG) protects remote users from zero-day threats and data from exfiltration when they access the internet. It provides secure, continuous web connectivity for every device, user, and location. With integrated cloud access security broker (CASB) capabilities, a comprehensive, advanced data loss prevention (DLP) engine, and integrated remote browser isolation (RBI) at no extra cost.
PRODUCT DESCRIPTION
With the volume and variety of internet threats increasing today, cloud-native SWGs have become indispensable for any organization that seeks to build security resilience—andespecially for those that are on a cloud transformation journey and have adopted a hybrid or fully remote work model. Organizations are concerned about cloud or network outages, which may impact performance, lack of control over and visibility into the cloud operations, and protection for sensitive corporate data stored, used, and shared in the cloud.
Cloud-native Skyhigh SWG allays those concerns by extending protection between the boundaries of the corporate network, enabling secure web connectivity for every device, user, and location. As part of the Skyhigh Cloud Platform, Skyhigh SWG brings elevated security to your network and cloud transformation with infinitely scalable cloud capacity—without the need for expensive, high-maintenance appliances. As a best-in-class solution, Skyhigh SWG delivers exceptional performance and 99.999% availability, along with the industry’s leading advanced threat protection capabilities, to ensure minimal latency and robust security.
Centrally managed Skyhigh SWG applies the same consistent policies and level of protection when your users go to the cloud, regardless of whether they are working from home or at remote offices.
To further simplify your technology stack and minimize management complexity, Skyhigh SWG converges fully with your SD-WAN. And, if mergers and acquisitions (M&A) are on the horizon, you’ll find it easy to add new users and get them up and running quickly.
Unmatched protection: DLP, threat protection, and RBI
Skyhigh SWG secures users and data with unified advanced protection. Its industry-leading DLP engine safeguards your sensitive data and users across all vectors: the web, Security-as-a-Service (SaaS), Infrastructure-as-a-Service (IaaS), and private applications. Integrated with Skyhigh SWG, the DLP engine protects sensitive data from flowing out of your organization or being accessed by the wrong people in real-time. This prevents your data from being uploaded to unauthorized websites.
DLP policies are enforced through multiple methods, and, if incidents arise, you can swiftly remediate issues based on severity through quarantine, deletion of malicious content, coaching users, and other techniques.
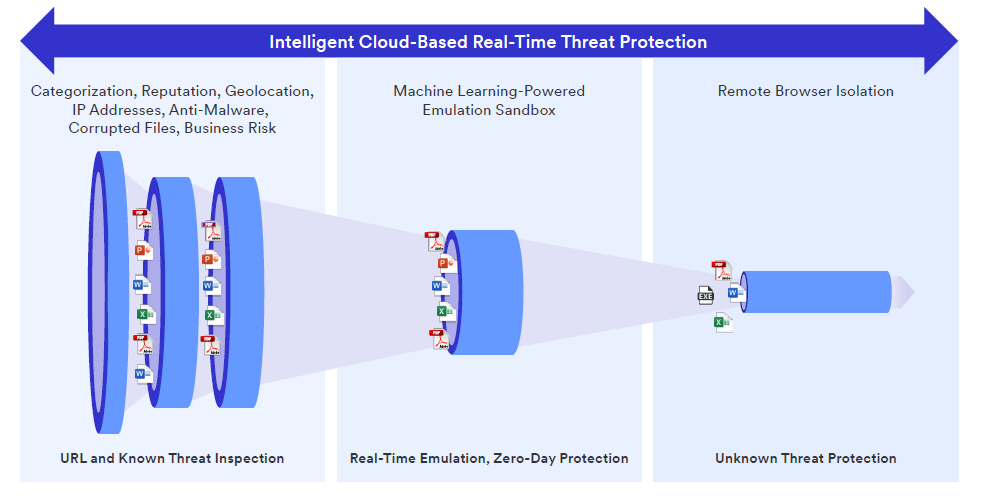
Enterprise-grade threat protection scans content for viruses and malware, detecting known or zero-day threats in real time. Emulation sandboxing stops threats in their tracks and isolates them from your environment, allowing you to analyze how they work and what you can do to stop them. Automated threat protection controls reduce the number of alerts and incidents that security teams need to respond to.
Consistent policies, data protection, and visibility across isolated and non-isolated traffic work together to help you improve overall operational efficiency. Since Skyhigh SWG fully converges with the Skyhigh Cloud Platform, you can add additional security services as required—all managed by the same console.
Skyhigh SWG for Hybrid: extend your onpremises policies to the cloud
Combine the strength of appliances with the power of the cloud. The hybrid deployment mode for Skyhigh SWG allows organizations the flexibility to move to the cloud at their own pace, while keeping the necessary onpremises appliances – all managed from a single console. This hybrid model extends the same classifications and security policies for web access for both on-premises and cloud users in just a single click. This means that you can enforce the same sophisticated policies for your entire hybrid workforce, while avoiding the additional time and effort of rewriting your policies from scratch. Skyhigh Security is the first, and one of the only, vendors to offer this powerful deployment mode.
Skyhigh Secure Web Gateway is part of the unified Skyhigh Cloud Platform that integrates multiple innovative security technologies—Zero Trust Private Access (ZTNA), Cloud Access Security Broker (CASB), Data Loss Prevention (DLP), and Remote Browser Isolation (RBI) —all managed from the same central console. The Skyhigh Cloud Platform enables fast, reliable, and safe work-from-anywhere and digital transformation by securing web, cloud, and private applications.
Being data-aware means that the Skyhigh Cloud Platform provides modern data protection policies for data in motion and data at rest that determine what can be accessed, what can be shared, and how it can be used. It goes beyond zero trust by monitoring user actions to identify risky behavior: sites visited, personal or work devices, employee or contractor, type of data, and many other factors. It ensures sensitive data is accessed, shared, and stored appropriately.
KEY USE CASES
- Protect users from malware and data loss with multi-layer security: scan all downloads against known and unknown threats with our machine learning-based emulation sandbox and against potentially malicious sites with RBI.
- Apply DLP policies to web traffic and sensitive data to prevent exfiltration of sensitive data to unsanctioned cloud applications while monitoring usage through a single, easy-to-use dashboard.
- Take advantage of predefined features, and augment them with your own use cases without waiting for product revisions.
FUNCTIONALITIES
- Exact data matching (EDM): Accurately fingerprints large structured data stores with billions of cells 1,000 times faster than other solutions and swiftly deploys data protection rules to prevent exfiltration and inappropriate sharing across all applications.
- Indexed document matching (IDM): Safeguards unstructured data in text documents and image files through fingerprinting and indexing. IDM detects proprietary information in PDFs, documents, JPEG images, and more. Once data is fingerprinted, you can add a DLP policy rule to leverage that indexed data and further reduce the risk of data loss.
- Optical character recognition (OCR): Extracts text out of documents and images and scans these for sensitive information, empowering you to prevent data misuse, loss, and theft.
- Cloud risk mitigation: Allows users to securely use the web and cloud apps from anywhere and stay productive.
- Application visibility and control: Blocks website access based on categories, reputation, or risk. It applies different policies to personal and corporate tenants, prevents potential infections and data loss, and enforces internet browsing policy. You gain expanded visibility and control over access to cloud applications, including Shadow IT.
- URL and category filtering: Blocks access to risky and/or malicious content and phishing sites and prevents malware.
LEARN MORE
https://www.gartner.com/en/documents/4013396
https://www.skyhighsecurity.com/en-us/lp/the-data-dilemma-cloud-adoption-1 and-risk-report.html
CONTACT US FOR DETAILS

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30