The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.
Cobalt Strike is a threat emulation tool perfect for mimicking advanced, hidden undesirable effects that have been embedded in your IT environment for a long time.
Cobalt Strike's post-exploitation agents and collaboration capabilities provide effective threat simulations. Measure incident response with malleable C2, which allows network metrics to mimic various malware to strengthen security operations to measure security program and have incident response capabilities.
TECHNOLOGY
Simulating the built-in threat actor:
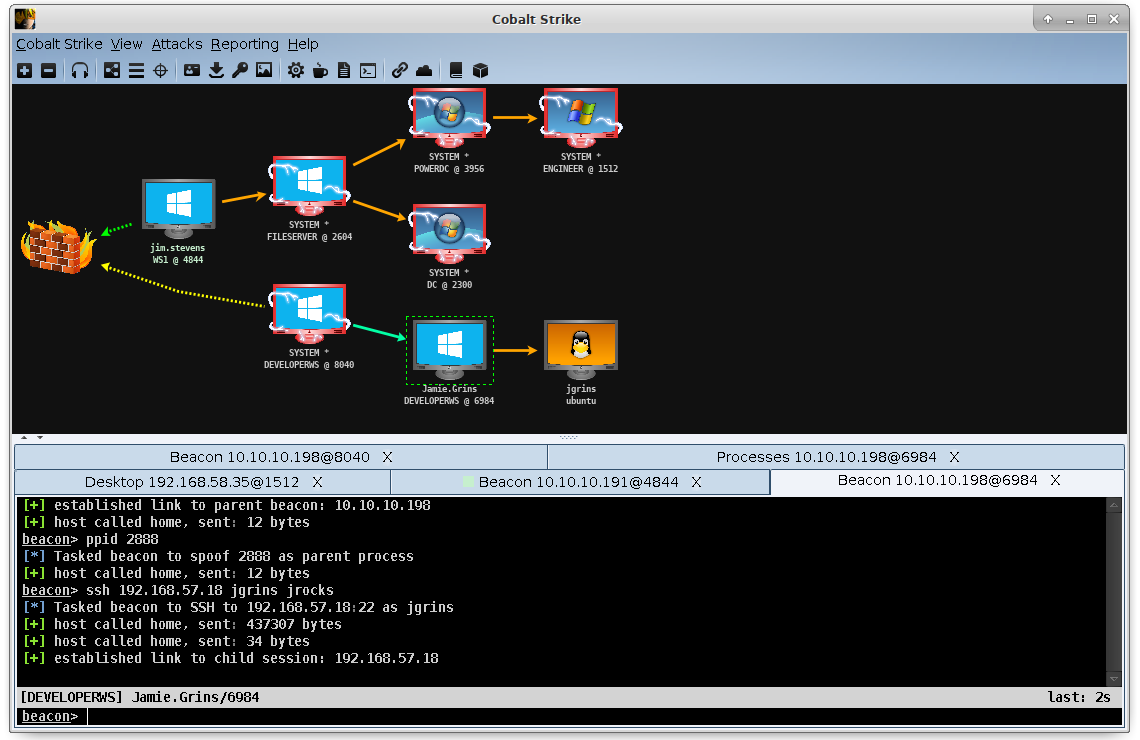
Once in service, the Cobalt Strike payload can be silently transmitted over HTTP, HTTPS or DNS, using asynchronous "low and slow" communication commonly used by built-in attackers who wish to remain undetected. With Malleable C2, Beacon's flexible command and control language, users can modify network pointers to blend in with normal traffic or hide their actions by emulating various types of malware. A beacon can perform a variety of post-exploitation activities, including executing PowerShell scripts, logging keystrokes, capturing screenshots, downloading files, and creating other payloads.
Gain an advantage with targeted attacks:
Starting by gathering information with the Cobalt Strike System Profiler, which maps the target's client-side attack surface, providing a list of applications and plug-ins that it discovers through the user's browser, as well as the internal IP address of users who are behind the proxy server. This advanced recognition makes it easier to determine the most effective attack path.
It has the ability to design an attack using one of the numerous Cobalt Strike packages. For example, organizing a drive-by attack using clones of websites. Alternatively, you can turn an innocent file into a Trojan horse using Microsoft Office macros or Windows executive files.
Customization of scripts and frameworks to specific needs:
Cobalt Strike is designed with flexibility in mind to meet all your needs. Users are encouraged to extend Cobalt Strike's capabilities by making changes to built-in scripts or introducing their own weapons. Additional modifications can be made to the Cobalt Strike client by scripting in its custom "Aggressor Script" scripting language.
Changes may also be made to kits downloaded from Cobalt Strike packages. Modification of the Artifact Kit, which is the source code used to generate executables and DLLs, or redefining the script templates included in the Resource Kit that Cobalt Strike uses in its workflows.
Convert engagement into comprehensive reports:
Cobalt Strike can generate multiple reports to provide you with a complete picture of all activities that took place during the execution of the order. Report types include:
- Timeline of activities
- Data summary per host
- Compromise indicators
- A full list of activities for all sessions
- Social engineering
- Tactics, techniques and procedures
Reports are exported in MS Word or as PDF and can be customized. You can add a custom logo as well as configure the title, description and hosts.
Streamlining key operations interoperability:
People with both Core Impact and Cobalt Strike can take advantage of session forwarding and tunneling between the two tools. This interoperability can further streamline penetration testing activities. For example, users can start their engagement by getting initial access from Core Impact, and then they can continue post-exploitation activities with Cobalt Strike by launching Beacon.
Why Cobalt Strike:
- Recognition on the client side
- Payload after use
- Secret communication
- Attack packets
- Browser switching
- Spear phishing
- Collaboration in the Red team
- Reporting and logging
ASK FOR DETAILS
IT solutions

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30














