The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Skyhigh Security Cloud Access Security Broker (CASB)
A cloud access security broker that protects data and prevents threats across SaaS, PaaS, and IaaS from a single, cloud-native enforcement point.
PRODUCT DESCRIPTION
A cloud access security broker that protects data and prevents threats across SaaS, PaaS, and IaaS from a single, cloud-native enforcement point. It offers:
- Visibility – Insight into all data and cloud usage.
- Control – Full control over data and cloud activity from any source.
- Protection – Defense against cloud threats and misconfigurations.
Skyhigh Security cloud platform offers:
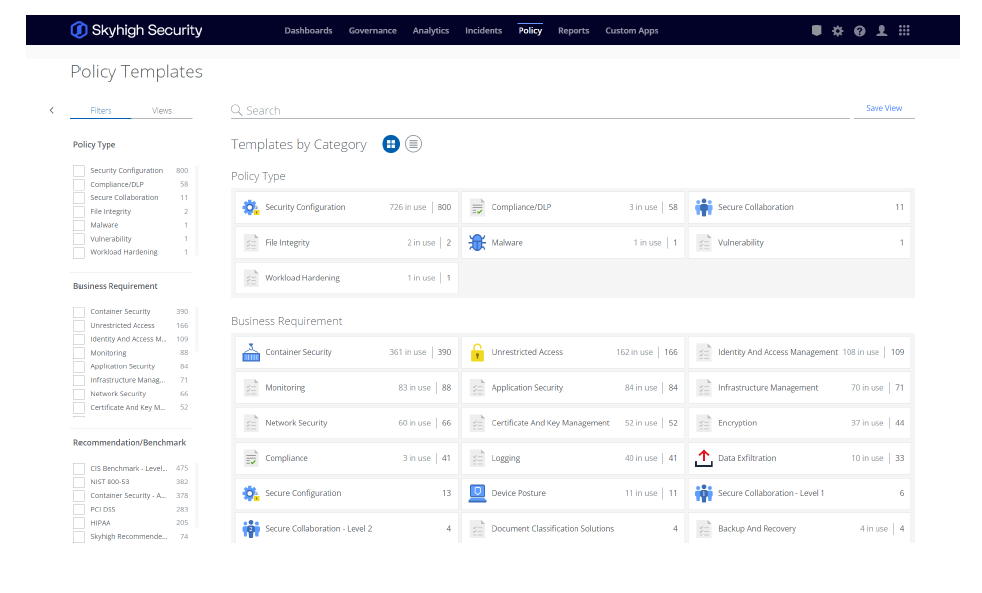
Unified policy engine
Applies unified policies to all cloud services across datavat rest and in transit. Leverage policy templates, import policies from existing solutions
or create new ones.
Pre-built policy templates
Delivers out-of-the-box policy templates based on business requirement, compliance regulation, industry, cloud service, and third-party benchmarks.
Policy creation wizard
Defines customized policies using rules connected by Boolean logic, exceptions, and multi-tier remediation based on incident severity.
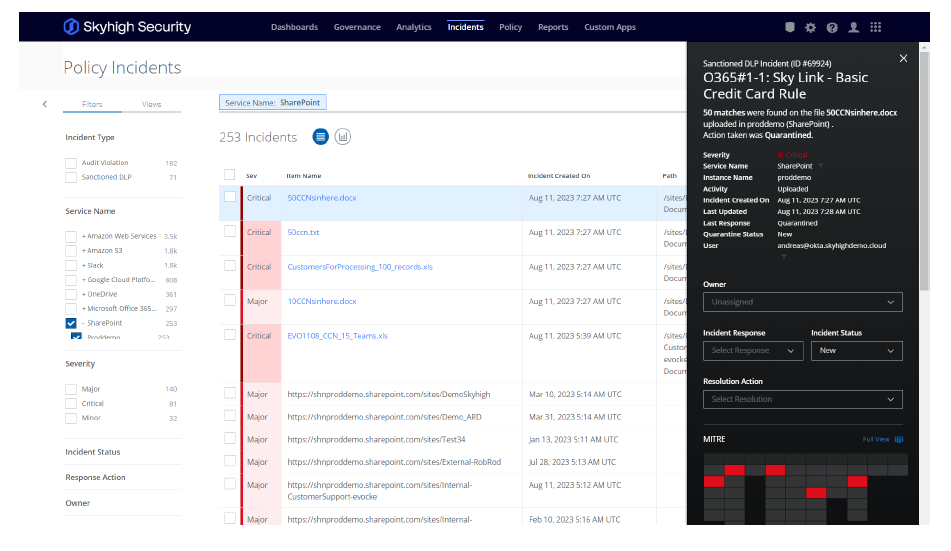
Policy incident management
A unified interface to review incidents, take manual action, and rollback automatic remediation actions to restore files and permissions.
Cloud Registry
Provides the world’s largest and most accurate registry of cloud services with a 1-10 CloudTrust Rating based on a 261-point risk assessment.
Multi-Cloud Protection
Enforce a uniform set of security policies across all cloud services, with the ability to associate policy violations and investigate activities,
anomalies, and threats at individual services.
Privacy Guard
Leverages an irreversible one-way process to tokenize user identifying information on premises and obfuscate enterprise identity.
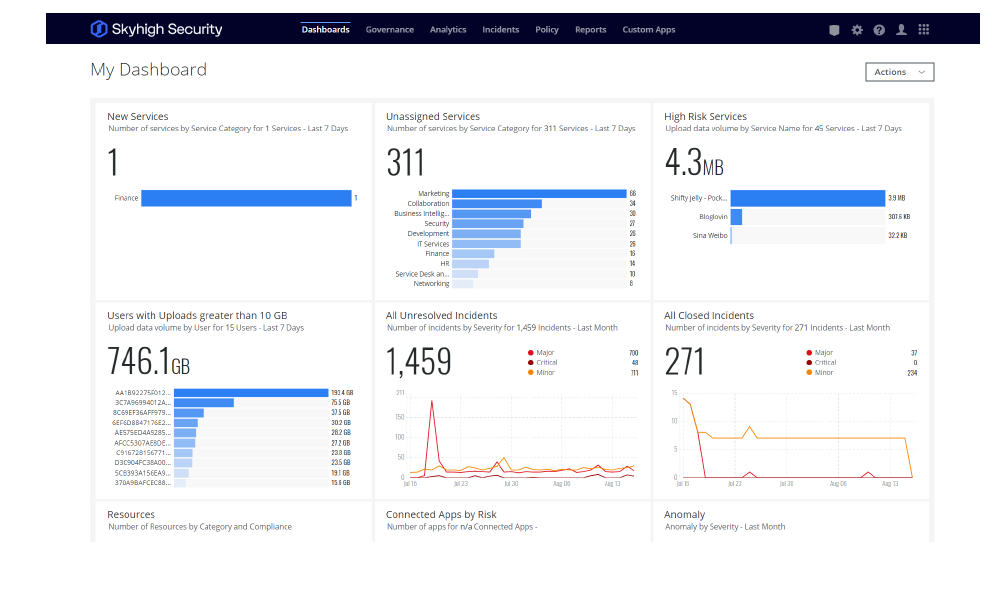
Visibility into all cloud use and data:
- Leverages keywords, pre-defined alphanumeric patterns, regular expressions, file metadata, document fingerprints, and database fingerprints to identify sensitive data in cloud services.
- Detects granular viewer, editor, and owner permissions on files and folders shared to
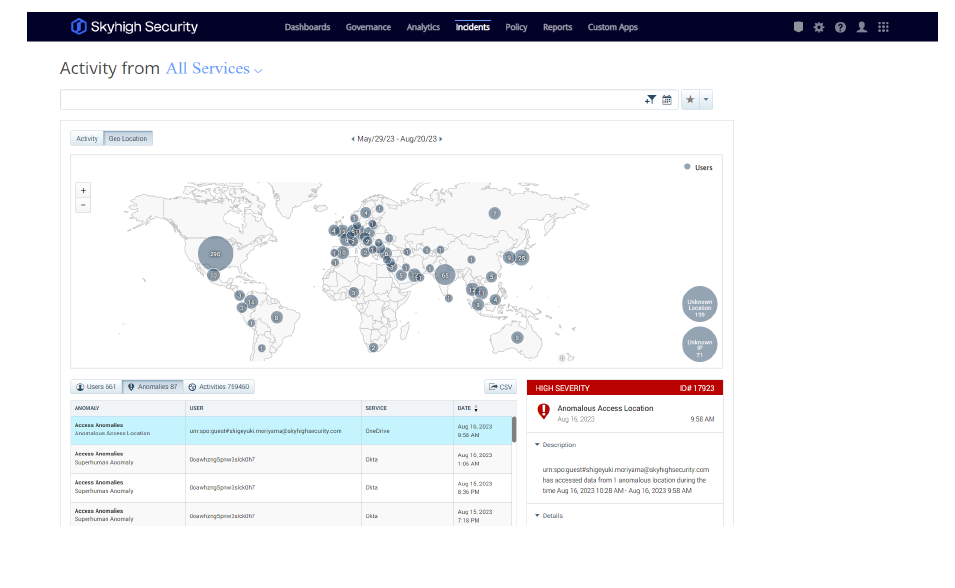
individual users, everyone in the organization or anyone with a link. - Understands access context including device operating system, device management status, location, and corporate/personal accounts.
- Summarizes cloud usage including cloud services in use by a user, data volumes, upload count, access count, and allowed/denied activity
over time. - Captures a comprehensive audit trail of all user and administrator activities to support postincident investigations and forensics.
Control Over Data and Activity in the Cloud:
- Enforces policies based on your own content rules to prevent data loss in cloud applications and infrastructure, across file, structured, and unstructured data. On-premises Skyhigh Security Data Loss Prevention (DLP), powered by Trellix.
- Enforces DLP policies for data uploaded to the cloud, created in the cloud, shared with collaborators, shared cloud-to-cloud from one
service to another, and downloaded from the cloud. - Defines policies with multiple levels of severity and enforces distinct response actions based on the severity level of the incident. Response actions, such as a DLP scan in real time, can be automatically triggered by a misconfiguration found in an audit.
- Isolates files that trigger policies in a secure administrative location within the cloud service where it was found. Skyhigh Security never
stores quarantined files.
ADDITIONAL FEATURES:
- Protects sensitive data with peer-reviewed, function preserving encryption schemes using customer controlled keys for structured and
unstructured data. - Applies rights management protection to files uploaded to or downloaded from cloud services, ensuring sensitive data is protected anywhere.
- Downgrades file and folder permissions for specified users to editor or viewer, removes permissions, and revokes shared links. Permissions can be based on sensitivity of data.
- Provides visibility into third-party applications connected to sanctioned cloud services, such as marketplace apps. Take policy-driven control over third-party apps based on specific users, applications, or access permissions.
- Permanently removes data from cloud services that violate policy, to comply with compliance regulations.
- Enforces coarse allow/block access rules based on service level risk, device type, and granular activity-level controls to prevent upload and download of data.
- Forces additional authentication steps in realtime via integration with identity management solutions based on access control policies.
- Granular policy for unsanctioned cloud services including the ability to allow or block activities and control access to unsanctioned tenants all from our console.
ENTERPRISE TECHNOLOGY INTEGRATIONS:
- Data loss prevention (DLP)
- Security information and event management (SIEM)
- Key management service(KMS)
- Identity and Access Management (IAM)
- Information rights management (IRM)
- Enterprise mobility management (EMM/MDM)
- Directory services (LDAP)
KEY USE CASES:
- Enforce data loss prevention (DLP) policies on data in the cloud, in sync with your endpoint DLP.
- Prevent unauthorized sharing of sensitive data to the wrong people.
- Block sync/download of corporate data to personal devices.
- Detect compromised accounts, insider threats, and malware.
- Gain visibility into unsanctioned applications and control their functionality.
- Audit for misconfiguration against industry benchmarks and automatically change settings.
- Container optimized strategies for securing dynamic and ever-changing container workloads and the infrastructure on which they depend.
CONTACT US FOR DETAILS
IT solutions

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30